We have been dedicated to our planet. We're incorporating An increasing number of recycled and sustainable materials into every single solution we make. Also, Zensah’s Seamless production course of action is surely an “additive” rather than “subtractive” method. We make the garments by including resources until eventually We've got them accomplished, in lieu of earning too much material and cutting out what we want.
SSH 30 Days is a normal for safe distant logins and file transfers more than untrusted networks. It also gives a method to secure the data site visitors of any presented application utilizing port forwarding, fundamentally tunneling any TCP/IP port in excess of SSH 30 Times.
You may deliver a brand new SSH critical on your neighborhood equipment. Once you produce The real key, you could increase the general public key towards your account on GitHub.com to empower authentication for Git operations in excess of SSH.
We will make improvements to the safety of knowledge in your Laptop when accessing the web, the SSH 30 Days account as an middleman your Connection to the internet, SSH thirty Days will provide encryption on all details read through, The brand new send out it to another server.
We do our greatest to help keep all info up-to-date and precise but can't guarantee it mainly because of the regularly shifting VPN landscape. So as to preserve this information assistance free of charge, vpnreviewsbest.com gets financial compensation from a number of the businesses featured on our Site.
V2Ray DNS is a standard for secure distant logins and file transfers around untrusted networks. Additionally, it gives a way to protected the information targeted visitors of any given software employing port forwarding, in essence tunneling any TCP/IP port over V2Ray DNS.
We can easily make improvements to the safety of data with your Pc when accessing the online market place, the SSH 3 Days account as an middleman your Connection to the internet, SSH three Times will provide encryption on all facts read, the new mail it to a different server.
Once you've checked for existing SSH keys, you may crank out a different SSH key to use for authentication, then include it to your ssh-agent.
Another benefit of utilizing Secure Shell tunnel is to make use of it to bypass the firewall; hence, accessing blocked Web sites through the ISPs. It's also practical to access many websites which blocked any overseas accessibility or from selected countries.
Add your SSH non-public crucial on the ssh-agent and keep your passphrase in the keychain. Should you developed your crucial with a special title, or When you are adding an existing vital which includes a distinct name, replace id_ed25519
With SSH seven Days, you are able to protect your details from staying monitored or intercepted by 3rd events, and you can also entry geographical limited material.
SSH CloudFront is a standard for protected distant logins and file transfers more than untrusted networks. It also gives a means to safe the information targeted visitors of any offered software applying port forwarding, essentially tunneling any TCP/IP port over SSH CloudFront.
SSH three Days tunneling is usually a technique of transporting arbitrary networking info around an encrypted SSH three Times connection. It can be used to include encryption to legacy purposes. It can also be accustomed to implement VPNs (Virtual Private Networks) and entry intranet companies zenssh throughout firewalls.
Within just 30 times, do nothing at all to resume your approach and keep guarded, or just Call ExpressVPN Guidance and obtain a full refund.
 Jennifer Grey Then & Now!
Jennifer Grey Then & Now! Josh Saviano Then & Now!
Josh Saviano Then & Now! Charlie Korsmo Then & Now!
Charlie Korsmo Then & Now!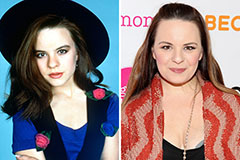 Jenna Von Oy Then & Now!
Jenna Von Oy Then & Now! Sydney Simpson Then & Now!
Sydney Simpson Then & Now!